
Today, every business or organization – no matter the size – is at risk of a ransomware attack. Governments, private sector businesses and even tech companies (companies you think would know how to protect themselves) have faced debilitating cyberattacks in recent months. The cost of these attacks is staggering. In 2021 alone, ransomware victims paid more than $600 million to cybercriminals. To put that number into perspective, the average of these payments reached $812,000 – up from an average payment of $170,000 in 2020.
A Tech Giant Falls Victim
Cisco ranks number 63 on the Fortune 100 with $49 billion in revenue. But on August 10, 2022, Cisco confirmed that its corporate network had been breached by the Yanluowang ransomware group in May of 2021. According to the threat actor, 2.75GB of data had been stolen, including everything from NDAs to engineering drawings.
How could a company like Cisco fall victim to this attack? All it took was one employee. The threat actors hijacked an employee’s personal Google account and found credentials synced from their browser. From there, the attacker tricked the employee into accepting a phony multi-factor authentication (MFA) push notification. That’s all it took for the threat actor to get its foot in the door of the company’s network and then into the company’s servers and domain controllers.
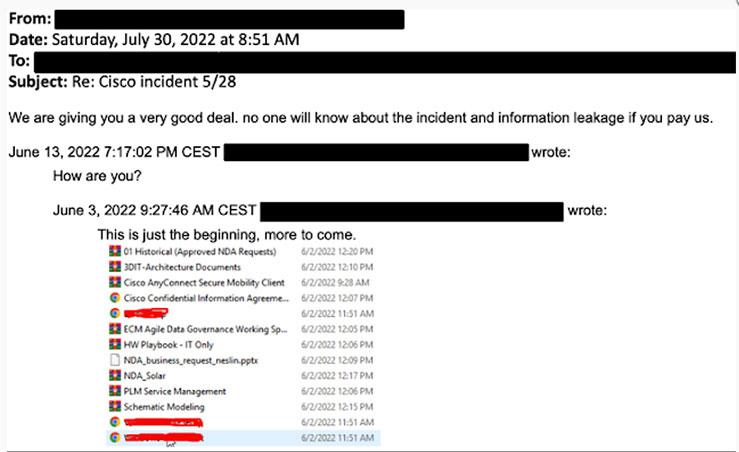
Eventually, Cisco detected the attackers and successfully evicted them from their digital environment. However, over the following weeks, the attackers continued to try to regain access to Cisco’s network.
You Don’t Have to Be Big to Get Hacked
While it makes sense for threat actors to go after the big guys (the bigger the company, the bigger the potential ransom), mid-sized organizations face the same risks. In 2021, 66% of mid-sized organizations worldwide found their digital landscape had fallen victim to cyberattacks – an increase of 37% over 2020. Worse still, 46% of these breached companies paid a ransom. As mentioned above, the average payment reached $812,000 in 2021.
Entire Countries Face Risks
Over the past two months, Costa Rica has been crippled by two major ransomware attacks. Declaring the attacks a national emergency (the first time that a country has ever called a cyberattack a “national emergency”), the breaches have crippled many essential services, halted international trade and cost the country millions as the affected organizations have had to perform their work on paper instead of on computers. According to Costa Rica’s president Rodrigo Chaves, the first attack targeted 27 government bodies, while the second attack focused on the country’s healthcare system.
Allegedly perpetrated by the Conti hacking group, the attacker demanded a $10 million ransom payment, which later ballooned to $20 million when no ransomware payments were made.
Bounties on Attackers
In addition to targeting Costa Rica, Conti has also attacked hospitals and businesses around the world. Their estimated ransomware earnings totaled over $180 million last year alone. Conti has become so dangerous, that the US State Department announced bounties of up to $10 million for anyone who provides useful information about individual members of Conti.

How to Protect Your Business
Cyberattacks can be devastating and costly to an organization – and the threats are continuing to evolve and become more malicious. When it comes to protecting your digital environment, prevention is the best medicine. The United States Computer Emergency Readiness Team (US-CERT) recommends a number of measures to protect your networks from ransomware infection:
- Establish a data backup and recovery plan. Make sure to have a plan for all critical information. By performing backups on a regular basis, you’ll limit the effects of data loss and help to expedite the recovery process. Also, since any backup connected to your network can still be at risk for ransomware, you’ll want to isolate your most important backups from the network. It is also important for backups to be immutable (they cannot be changed) to help in preventing a ransomware attacker from also attacking your backups.
- Install the latest patches. Many attacks target applications and operating systems. To protect against these attacks, make sure you keep your operating system and software up to date by installing the latest patches.
- Use the latest endpoint protection software and make sure it’s up to date.
- Restrict privileges. Limit the ability of people within your organization to install software on their own. Restricting these privileges may help to stop malware from running or limit its ability to breach your network. Where users do require admin privileges, they should not always work with elevated privileges. Most operating systems now follow this approach, where you need to enter a password in order to use admin privileges.
- Safeguard emails. Make sure everyone in your organization knows to NOT click any links in emails or download attachments unless they trust the sender. This requires training. It is also worth considering less subtle measures, like inserting headers into external emails to make sure that users are aware of them.
To Pay or Not to Pay a Ransom?
US-CERT discourages organizations from paying ransomware. The main reason is that paying the ransom doesn’t guarantee that the threat won’t be carried out. However, US-CERT also acknowledges that you may not be able to retain your data without paying a ransom if you fall victim to Cryptolocker, Cryptowall or other sophisticated ransomware. As always, the first step to defending your cyber landscape is a strong offense. Follow the tips above and always stay vigilant. It may not be easy but staying one step ahead of threat actors can help to protect your business from expensive ransomware attacks.